For those admins that are trying to keep a lock down on who gets out to the internet, here's a warning, there's a new way to get out to HTTP sites, if you have access to an SMTP server.
From: https://www.infosecisland.com/blogview/3447-Http-over-SMTP-Proxy.html
In some cases you find your self in need of a way to navigate the website and you have no internet connection.
Hosproxy is a tool designed to let you access the web in a LAN without internet connection but with access to an E-mail system only.
This tool consists of two parts:
• HosTunnel: You need an external server (outside LAN) which must be running HoSTunnel (with root privileges to listen on port 25) and which receives and sends emails with encoded and packaged http requests/responses.
• HoSProxy: An internal proxy connected to the web browser, that sends HTTP request trough emails via the company SMTP server, and polls for responses in the company POP/IMAP server.
For configuration you only need to configure HoSProxy, not HosTunnel. HoSProxy contains the following config file (hosproxy.cfg)
[CFG]
# Your smtp server for outgoing mails, for example:
#smtp.myserver.com
local_smtp_server=
# Y or N
smtp-auth=N
smtp-user=cdelojo@edge-security.com
smtp-pass=
# Specify your Mail access server protocol (pop, imap,
#imapssl, popssl)
mail_retrieve_protocol=pop
# Your mail access server server for incoming mails, for
#example: pop3.myserver.com
mail_access_server=
#Your username to connect to your mail access server
mas_user=cdelojo@edge-security.com
#YOUR PASSWORD WILL BE PROMPTED IF YOU WANT but you can
#configure it
mas_passwd=
#Your email, account used for recive http responses
email=cdelojo@edge-security.com
#This is the e-mail address to send the HTTP-requests, the
#user name can be random eg. asdf@external-server.com
ext_email=asdf@ligual.net
Run hosproxy.exe and you can browse any site.
Welcome to the Proxy Update, your source of news and information on Proxies and their role in network security.
Wednesday, March 31, 2010
Monday, March 29, 2010
Rustock Botnet Using TLS Encryption to Push Spam
PCWorld reported that the volume of spam being sent by the notorious Rustock botnet using TLS encryption has surged in recent weeks, establishing an important new trend in botnet behavior, security companies have said.
Two weeks ago, Symantec's MessageLabs division reported noticing large volumes of spam using TLS (Transport Layer Security), an encryption protocol successor to the better-known SSL (Secure Sockets Layer), and normally a way of securing the contents of an email between server and client.
At that point, the percentage of spam encrypted by Rustock using TLS was around the 35 percent mark, a figure the company says in its latest Intelligence Report this week has surged to as much as 77 percent of its activity during the month.(See "Don't be Dragooned into the Botnet Army.")
The challenge is that TLS imposes higher processing demands on mail servers compared to non-TLS traffic, estimated to be around 1 kilobyte overhead for every spam email. Given that most email is now spam, the accumulated overhead on mail servers has the potential to be high whether the messages are detected as spam or not.
Rustock itself is a top three player in the botnet stakes, responsible for various huge spam campaigns since it first appeared in 2008. It was one of the bots said to have been most affected by the closing of McColo in early 2009, a trauma that might have had some bearing on the latest self-defence evolution.
MessageLabs is not the only hosted messaging provider to notice Rustock's use of TLS. Around the same time as the company put out its first Rustock warning, a blog by Terry Zink of Microsoft's Forefront Online Security division mentioned a similar issue with Rustock and its use of the TLS protocol.
Other providers contacted by Techworld this week reported seeing more TLS-encrypted spam included CronLab of Sweden and US-UK messaging outfit, M86 Security.
"We set up a node in our Labs with TLS and confirmed that some Rustock botnets were indeed using TLS," said Phil Hay, a spam expert at M86 Security. "Our statistics show that Rustock is still the leading source of spam output and this new use of TLS highlights an escalating level of sophistication."
"In essence this means that organisations can't rely on enforcing TLS as a means for reducing spam. It does have an effect on system resources however, as all forms of encryption do," said Hay.
Why Rustock has adopted this technique is open to debate. Adding TLS to outbound spam slows the rate at which spam can be delivered, which would seem to hurt the spammer's intention to spread non-legitimate email as far and fast as possible. It is also the case that TLS-encrypted email is no longer automatically trusted by receiving servers, so it is unlikely to be a simple evasion technique.
Experts such as Zink speculate that it could be connected to the recent clampdown on several botnets by law enforcement, including the bust that led police in Spain to arrest three men accused of running the Mariposa botnet. Infiltrating Mariposa - indeed infiltrating any botnet - involves cracking its command and control layer. TLS could be a defence that makes such interception harder.
[Editor's note: While this refers to email based spam; it appears that increasingly malware is using SSL based transport, making SSL (and TLS) just as dangerous as in the clear connections. SSL proxies that check for malware will become increasingly important in fighting these threats]
Two weeks ago, Symantec's MessageLabs division reported noticing large volumes of spam using TLS (Transport Layer Security), an encryption protocol successor to the better-known SSL (Secure Sockets Layer), and normally a way of securing the contents of an email between server and client.
At that point, the percentage of spam encrypted by Rustock using TLS was around the 35 percent mark, a figure the company says in its latest Intelligence Report this week has surged to as much as 77 percent of its activity during the month.(See "Don't be Dragooned into the Botnet Army.")
The challenge is that TLS imposes higher processing demands on mail servers compared to non-TLS traffic, estimated to be around 1 kilobyte overhead for every spam email. Given that most email is now spam, the accumulated overhead on mail servers has the potential to be high whether the messages are detected as spam or not.
Rustock itself is a top three player in the botnet stakes, responsible for various huge spam campaigns since it first appeared in 2008. It was one of the bots said to have been most affected by the closing of McColo in early 2009, a trauma that might have had some bearing on the latest self-defence evolution.
MessageLabs is not the only hosted messaging provider to notice Rustock's use of TLS. Around the same time as the company put out its first Rustock warning, a blog by Terry Zink of Microsoft's Forefront Online Security division mentioned a similar issue with Rustock and its use of the TLS protocol.
Other providers contacted by Techworld this week reported seeing more TLS-encrypted spam included CronLab of Sweden and US-UK messaging outfit, M86 Security.
"We set up a node in our Labs with TLS and confirmed that some Rustock botnets were indeed using TLS," said Phil Hay, a spam expert at M86 Security. "Our statistics show that Rustock is still the leading source of spam output and this new use of TLS highlights an escalating level of sophistication."
"In essence this means that organisations can't rely on enforcing TLS as a means for reducing spam. It does have an effect on system resources however, as all forms of encryption do," said Hay.
Why Rustock has adopted this technique is open to debate. Adding TLS to outbound spam slows the rate at which spam can be delivered, which would seem to hurt the spammer's intention to spread non-legitimate email as far and fast as possible. It is also the case that TLS-encrypted email is no longer automatically trusted by receiving servers, so it is unlikely to be a simple evasion technique.
Experts such as Zink speculate that it could be connected to the recent clampdown on several botnets by law enforcement, including the bust that led police in Spain to arrest three men accused of running the Mariposa botnet. Infiltrating Mariposa - indeed infiltrating any botnet - involves cracking its command and control layer. TLS could be a defence that makes such interception harder.
[Editor's note: While this refers to email based spam; it appears that increasingly malware is using SSL based transport, making SSL (and TLS) just as dangerous as in the clear connections. SSL proxies that check for malware will become increasingly important in fighting these threats]
Monday, March 22, 2010
McAfee Makes Cloud Computing Security Play
From: http://www.eweek.com/c/a/Security/McAfee-Makes-Cloud-Computing-Security-Play-649121/?kc=rss
McAfee is taking a swing at securing cloud environments with a new service aimed at software-as-a-service providers.
Dubbed the McAfee Cloud Secure program, the service is essentially designed to compliment annual audits of security and process controls many cloud vendors undergo for certification purposes. With McAfee Cloud Secure, McAfee officials said they will partner with certification providers and offer an additional layer of security by providing a daily scan of application, network perimeter and infrastructure vulnerabilities.
Those that pass will receive a "McAfee SECURE" stamp of approval.
Securing cloud environments was one of the big topics at the RSAsecurity conference earlier this month. According to a survey by IDCon attitudes towards the cloud, 87.5 percent of participants said security concerns were the most significant challenges to cloud adoption.
"SAAS vendors have a difficult time convincing prospects that their services are secure and safe," said IDC analyst Christian Christiansen in a statement.
The McAfee offering is a step in the right direction however, he said.
While McAfee and other vendors have talked in the past about providing security from the cloud, this announcement marks an example of a growing focus in the industry on providing solutions to secure cloud environments themselves.
“McAfee looks at the cloud really from three different angles, which is security from the cloud, in the cloud and for the cloud,” explained Marc Olesen, senior vice president and general manager of McAfee’s software-as-a-service business, in an interview with eWEEK.
“What’s really been out there today are (annual) process certification audits…that address the process controls and security controls that cloud providers have in place,” Olesen said. “This has typically been an ISO-27001 certification or an SAS-70 certification that cloud providers are using, and we feel that that’s very important, but it’s just a start.”
McAfee is taking a swing at securing cloud environments with a new service aimed at software-as-a-service providers.
Dubbed the McAfee Cloud Secure program, the service is essentially designed to compliment annual audits of security and process controls many cloud vendors undergo for certification purposes. With McAfee Cloud Secure, McAfee officials said they will partner with certification providers and offer an additional layer of security by providing a daily scan of application, network perimeter and infrastructure vulnerabilities.
Those that pass will receive a "McAfee SECURE" stamp of approval.
Securing cloud environments was one of the big topics at the RSAsecurity conference earlier this month. According to a survey by IDCon attitudes towards the cloud, 87.5 percent of participants said security concerns were the most significant challenges to cloud adoption.
"SAAS vendors have a difficult time convincing prospects that their services are secure and safe," said IDC analyst Christian Christiansen in a statement.
The McAfee offering is a step in the right direction however, he said.
While McAfee and other vendors have talked in the past about providing security from the cloud, this announcement marks an example of a growing focus in the industry on providing solutions to secure cloud environments themselves.
“McAfee looks at the cloud really from three different angles, which is security from the cloud, in the cloud and for the cloud,” explained Marc Olesen, senior vice president and general manager of McAfee’s software-as-a-service business, in an interview with eWEEK.
“What’s really been out there today are (annual) process certification audits…that address the process controls and security controls that cloud providers have in place,” Olesen said. “This has typically been an ISO-27001 certification or an SAS-70 certification that cloud providers are using, and we feel that that’s very important, but it’s just a start.”
Wednesday, March 17, 2010
Blended threats demand new security approac
From: http://www.computerweekly.com/Articles/2010/03/12/240595/Blended-threats-demand-new-security-approach-says-Websense.htm
Blended threats are the chief online security risk to enterprises and a new approach is needed to defend against these threats, says security firm Websense.
These attacks are difficult to detect and block using traditional approaches to security, said Devin Redmond, vice-president of product management at Websense.
"Cybercriminals are increasingly using a whole range of attack methods blended together to steal valuable corporate data," he said.
A typical attack may use a targeted, personalised e-mail from a known contact that contains an embedded link to a malicious website that installs an information-stealing Trojan that sends out information using an encrypted protocol.
"The only way for enterprises to defend against these kinds of attacks without disrupting the business is to inspect everything that goes in and out," said Redmond.
Blocking certain categories of e-mails or collaboration channels such as social networking sites and cloud-based services is not a viable option, he said.
Security professionals must find a way of enabling the business to use the growing number of electronic communication channels and cloud services, but in a secure way, said Redmond.
"The business will use these channels regardless, so IT security professionals need to get involved to ensure processes are put in place to guard against data leaks," he said.
According to Redmond, the attacks against Google and more than 20 other companies disclosed in December would have been prevented if comprehensive content filtering systems had been in place.
"By monitoring and analysing outgoing data as well as incoming data, organisations can more easily detect and stop data leaks," he said.
Improving data visibility to enable greater control was a key theme at the co-located Forrester EMEA 2010 Security Forum and Infrastructure & Operations Forum in London, said Redmond.
Blended threats are the chief online security risk to enterprises and a new approach is needed to defend against these threats, says security firm Websense.
These attacks are difficult to detect and block using traditional approaches to security, said Devin Redmond, vice-president of product management at Websense.
"Cybercriminals are increasingly using a whole range of attack methods blended together to steal valuable corporate data," he said.
A typical attack may use a targeted, personalised e-mail from a known contact that contains an embedded link to a malicious website that installs an information-stealing Trojan that sends out information using an encrypted protocol.
"The only way for enterprises to defend against these kinds of attacks without disrupting the business is to inspect everything that goes in and out," said Redmond.
Blocking certain categories of e-mails or collaboration channels such as social networking sites and cloud-based services is not a viable option, he said.
Security professionals must find a way of enabling the business to use the growing number of electronic communication channels and cloud services, but in a secure way, said Redmond.
"The business will use these channels regardless, so IT security professionals need to get involved to ensure processes are put in place to guard against data leaks," he said.
According to Redmond, the attacks against Google and more than 20 other companies disclosed in December would have been prevented if comprehensive content filtering systems had been in place.
"By monitoring and analysing outgoing data as well as incoming data, organisations can more easily detect and stop data leaks," he said.
Improving data visibility to enable greater control was a key theme at the co-located Forrester EMEA 2010 Security Forum and Infrastructure & Operations Forum in London, said Redmond.
Tuesday, March 16, 2010
Are you a victim of an Injected malicious hidden Iframe?
From: http://research.zscaler.com/2010/03/are-you-victim-of-injected-malicious.html
People surf to a number of web pages throughout the day - online shopping, banking, social networking, search engines, etc. But do they know when something bad is happening behind the web page visible in their browser? A large number of legitimate web sites have been victim of attacks, where the payload modifies the pages on the website to include hidden Iframes to malicious content. This content is processed by the browser, transparent to the user, and can compromise the user’s system if they are running vulnerable client applications (for example, the browser itself, browser plug-ins, Adobe Acrobat reader, and Flash player).
Malicious Iframe attacks are not new but remain heavily used to carry out different attacks. HTML Iframe tags are used to embed content into the web page from a particular source, including sources external from the actual web site. Attackers are using zero pixel Iframes embed malicious content while to keeping content hidden from the user. People are often become victims from such attacks as it is easy to inject such malicious Iframes into a legitimate webpage by taking advantage of web application vulnerabilities like SQL injection.
Let’s walk through live example where a malicious Iframe has been injected in the webpage. Here is the screenshot of one of the website injected by Iframe,

The above screenshot shows obfuscated JavaScript is present in the webpage after the closing html “” tag (prior to the actual page body). Malzilla a user friendly GUI tool was used to decode the obfuscated JavaScript. You can find good documentation on their website.

Interestingly, the JavaScript decodes into another obfuscated JavaScript. There is small function called dF() and a call to the “document.write()” function. Below is a screenshot of decoding this further:
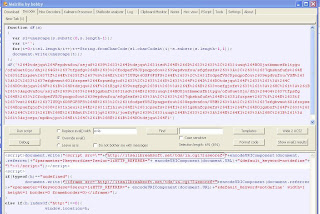
After decoding a second time, the JavaScript is clear and readable. This hidden injected Iframe embeds this JavaScript within the page, and when someone visits the page the JavaScript is processed by the browser, transparent to the user. If you look at the height and width of the Iframe, it is set to 1 pixel, which will not be seen by the user.
The above live example used multiple obfuscation techniques to hide the functionality of the malicious JavaScript. We have seen a number of websites infected with the same JavaScript code. The above example used “document.write()” function to write the malicious script into the page. Below is a decoded single obfuscated JavaScript example, which is still present on many websites:

Attackers are using simple to complex obfuscation techniques to encode their malicious script. Due to this, many Antivirus engines are unable to detect new injected Iframes. Here are the Virustotal results for the first example showing very low detection. Here is the third example of injected obfuscated script:

There are some important points to be considered here.
* In the past, it was common for attackers to inject their malicious Iframes at the bottom / end of the webpage. Attackers are now injecting malicious Iframes anywhere in the webpage.
* Many websites which were found to be infected in past months by malicious hidden Iframes appear to still be infected with them. Meaning most web site owners or hosting providers are not policing the content that they are serving on the web.
Our data shows many previously infected websites are still infected with hidden malicious Iframes today. Due to different obfuscation techniques detection by Antivirus vendors remains poor. This shows that even if it is a well-known attack, people are still at risk of being compromised. Web site owners and hosting providers should regularly patch any 3rd party web applications used to avoid known vulnerabilities (such as SQL injection), and regularly inspect their web pages for unauthorized modification (to include these malicious Iframes). Look out for obfuscated JavaScript within webpage’s, and for additions made prior to or following the HTML body tags. Users should patch all client applications (browsers, browser plug-ins, Adobe Acrobat, Flash, Java, Microsoft Office, etc.) used to view content pulled from the web. Additionally users can inspect the source of webpage and report compromised sites to the web site owner or hosting provider.
Start acting now. Be Safe while surfing!
People surf to a number of web pages throughout the day - online shopping, banking, social networking, search engines, etc. But do they know when something bad is happening behind the web page visible in their browser? A large number of legitimate web sites have been victim of attacks, where the payload modifies the pages on the website to include hidden Iframes to malicious content. This content is processed by the browser, transparent to the user, and can compromise the user’s system if they are running vulnerable client applications (for example, the browser itself, browser plug-ins, Adobe Acrobat reader, and Flash player).
Malicious Iframe attacks are not new but remain heavily used to carry out different attacks. HTML Iframe tags are used to embed content into the web page from a particular source, including sources external from the actual web site. Attackers are using zero pixel Iframes embed malicious content while to keeping content hidden from the user. People are often become victims from such attacks as it is easy to inject such malicious Iframes into a legitimate webpage by taking advantage of web application vulnerabilities like SQL injection.
Let’s walk through live example where a malicious Iframe has been injected in the webpage. Here is the screenshot of one of the website injected by Iframe,

The above screenshot shows obfuscated JavaScript is present in the webpage after the closing html “” tag (prior to the actual page body). Malzilla a user friendly GUI tool was used to decode the obfuscated JavaScript. You can find good documentation on their website.

Interestingly, the JavaScript decodes into another obfuscated JavaScript. There is small function called dF() and a call to the “document.write()” function. Below is a screenshot of decoding this further:

After decoding a second time, the JavaScript is clear and readable. This hidden injected Iframe embeds this JavaScript within the page, and when someone visits the page the JavaScript is processed by the browser, transparent to the user. If you look at the height and width of the Iframe, it is set to 1 pixel, which will not be seen by the user.
The above live example used multiple obfuscation techniques to hide the functionality of the malicious JavaScript. We have seen a number of websites infected with the same JavaScript code. The above example used “document.write()” function to write the malicious script into the page. Below is a decoded single obfuscated JavaScript example, which is still present on many websites:

Attackers are using simple to complex obfuscation techniques to encode their malicious script. Due to this, many Antivirus engines are unable to detect new injected Iframes. Here are the Virustotal results for the first example showing very low detection. Here is the third example of injected obfuscated script:

There are some important points to be considered here.
* In the past, it was common for attackers to inject their malicious Iframes at the bottom / end of the webpage. Attackers are now injecting malicious Iframes anywhere in the webpage.
* Many websites which were found to be infected in past months by malicious hidden Iframes appear to still be infected with them. Meaning most web site owners or hosting providers are not policing the content that they are serving on the web.
Our data shows many previously infected websites are still infected with hidden malicious Iframes today. Due to different obfuscation techniques detection by Antivirus vendors remains poor. This shows that even if it is a well-known attack, people are still at risk of being compromised. Web site owners and hosting providers should regularly patch any 3rd party web applications used to avoid known vulnerabilities (such as SQL injection), and regularly inspect their web pages for unauthorized modification (to include these malicious Iframes). Look out for obfuscated JavaScript within webpage’s, and for additions made prior to or following the HTML body tags. Users should patch all client applications (browsers, browser plug-ins, Adobe Acrobat, Flash, Java, Microsoft Office, etc.) used to view content pulled from the web. Additionally users can inspect the source of webpage and report compromised sites to the web site owner or hosting provider.
Start acting now. Be Safe while surfing!
Monday, March 15, 2010
'Cybercrime exceeds drug trade' myth exploded
This is a little dated (from Mar 29, 2009), but thought it was interesting enough for a repost here. It's from: http://www.theregister.co.uk/2009/03/27/cybercrime_mythbusters/
A leading security researcher has unpicked the origins of the myth that revenues from cybercrime exceeds those from the global drug trade, regurgitated by a senior security officer at AT&T before Congress last week.
Ed Amoroso, Senior Vice President and Chief Security Officer of AT&T, told a Congressional Committee on 20 March that cybercrime was a $1trn a year business. It'd be nice to think that Amoroso had been misquoted or made a slip of the tongue but written testimony from Amoroso repeats the amazing claim, made before a hearing of the Senate Commerce, Science, and Transportation Committee.
The end of paragraph 5 of the written submission states:
Last year the FBI announced that revenues from cyber-crime, for the first time ever, exceeded drug trafficking as the most lucrative illegal global business, estimated at reaping more than $1 trillion annually in illicit profits.
As Richard Stiennon points out the quoted figure would make cybercrime bigger than the entire IT industry. The top 10 Fortune 50 firms turned over $2trn last year.
Put another way, revenues from cybercrime exceed those of AT&T itself ($119bn in 2008) by a factor of around eight.
Estimates of the drug trade peg annual revenues at about $400bn. There's no figure on this from the FBI much less a comparative figure comparing cybercrime and drug trade revenues, despite what Amoroso said.
Stiennon, chief research analyst at IT-Harvest, guesses that cybercrime profits might be worth about $1bn a year, which seems much more plausible.
You'd have to be on something truly mindblowing to think that cybercrime revenues exceed the GDP of Saudi Arabia ($555bn in 2007), with all its oil income.
How could anyone ever think such a thing? Stiennon comes up trumps in tracking down the origin of this meme.
The idea that cybercrime revenue trumps that of the drug trade were first mentioned by Valerie McNiven, a consultant to the US Treasury Department in November 2005. The figure cited at the time was the still-implausible $105bn, Stiennon reports.
The same figure, mentioned by a lawyer to a Reuters stringer and henceforth enshrined in clippings harvest by the PR departments of security firms, reappeared again in a September 2007 speech by the chief exec of McAfee, David DeWalt.
Eighteen months later the meme has grown so that the figure cited is $1trn but, as Stiennon points out, the form of language is virtually identical. Earlier this week security firm Finjan published a press release ("Finjan confirms cybercrime revenues exceeding drug trafficking") supporting the myth, most recently relayed by Amoroso before Congress.
We asked Finjan whether it wanted to rethink what it said. Not a bit of it, the security firm responded.
"In our Q1 2009 report on cybercrime, for example, we revealed that one single rogueware network are raking in $10,800 a day, or $39.42 million a year," it said. "If you extrapolate those figures across the many thousands of cybercrime operations that exist on the internet at any given time, the results easily reach a trillion dollars."
You can observe the ongoing capers of this implausible FUD-laden cybercrime revenues meme in Stiennon's posting on the ThreatChaos blog here. ®
Bootnote
We're aware that even leaving aside Finjan's head-spinning statistical assumptions its figures still don't stack up. When we called it to ask if it wanted to reconsider its earlier statement, contained in a press release but not published on its website, in light of Stiennon's criticism it answered that it was sticking by its guns.
A leading security researcher has unpicked the origins of the myth that revenues from cybercrime exceeds those from the global drug trade, regurgitated by a senior security officer at AT&T before Congress last week.
Ed Amoroso, Senior Vice President and Chief Security Officer of AT&T, told a Congressional Committee on 20 March that cybercrime was a $1trn a year business. It'd be nice to think that Amoroso had been misquoted or made a slip of the tongue but written testimony from Amoroso repeats the amazing claim, made before a hearing of the Senate Commerce, Science, and Transportation Committee.
The end of paragraph 5 of the written submission states:
Last year the FBI announced that revenues from cyber-crime, for the first time ever, exceeded drug trafficking as the most lucrative illegal global business, estimated at reaping more than $1 trillion annually in illicit profits.
As Richard Stiennon points out the quoted figure would make cybercrime bigger than the entire IT industry. The top 10 Fortune 50 firms turned over $2trn last year.
Put another way, revenues from cybercrime exceed those of AT&T itself ($119bn in 2008) by a factor of around eight.
Estimates of the drug trade peg annual revenues at about $400bn. There's no figure on this from the FBI much less a comparative figure comparing cybercrime and drug trade revenues, despite what Amoroso said.
Stiennon, chief research analyst at IT-Harvest, guesses that cybercrime profits might be worth about $1bn a year, which seems much more plausible.
You'd have to be on something truly mindblowing to think that cybercrime revenues exceed the GDP of Saudi Arabia ($555bn in 2007), with all its oil income.
How could anyone ever think such a thing? Stiennon comes up trumps in tracking down the origin of this meme.
The idea that cybercrime revenue trumps that of the drug trade were first mentioned by Valerie McNiven, a consultant to the US Treasury Department in November 2005. The figure cited at the time was the still-implausible $105bn, Stiennon reports.
The same figure, mentioned by a lawyer to a Reuters stringer and henceforth enshrined in clippings harvest by the PR departments of security firms, reappeared again in a September 2007 speech by the chief exec of McAfee, David DeWalt.
Eighteen months later the meme has grown so that the figure cited is $1trn but, as Stiennon points out, the form of language is virtually identical. Earlier this week security firm Finjan published a press release ("Finjan confirms cybercrime revenues exceeding drug trafficking") supporting the myth, most recently relayed by Amoroso before Congress.
We asked Finjan whether it wanted to rethink what it said. Not a bit of it, the security firm responded.
"In our Q1 2009 report on cybercrime, for example, we revealed that one single rogueware network are raking in $10,800 a day, or $39.42 million a year," it said. "If you extrapolate those figures across the many thousands of cybercrime operations that exist on the internet at any given time, the results easily reach a trillion dollars."
You can observe the ongoing capers of this implausible FUD-laden cybercrime revenues meme in Stiennon's posting on the ThreatChaos blog here. ®
Bootnote
We're aware that even leaving aside Finjan's head-spinning statistical assumptions its figures still don't stack up. When we called it to ask if it wanted to reconsider its earlier statement, contained in a press release but not published on its website, in light of Stiennon's criticism it answered that it was sticking by its guns.
Wednesday, March 10, 2010
Are URL shorteners really dangerous?
From: http://research.zscaler.com/2010/03/are-url-shorteners-really-dangerous.html
There has been plenty of buzz about URL shorteners and security. URL shorteners have been described as a new attack vector since being popularized by social networks such as Twitter. I don't feel that URL shorteners are any more of a threat than their full length counterparts and here's why...
How URL shorteners work
The purpose of a URL shortener is to replace a log URL (e.g: http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html) with a shorter one (e.g: http://bit.ly/cikl0z). When a user clicks on http://bit.ly/cikl0z, he is redirected to http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html via an HTTP 301 redirection:
Existing defense mechanisms
All the existing in-browser (Google Safe Browsing in Firefox, Opera's Fraud Protection, etc.) or external (IDS, proxy, etc.) URL scanners are applied on both the initial short and redirected long URL requests. If the long URL is a known malicious site, it will be stopped whether or not the the user clicks directly on the long URL, or on a shortened URL.
Also, content inspection (Antivirus, Deep Packet inspection, etc.) is applied on both requests.
The use of URL shorteners and redirections does not require any new security inspection. All of the web browser security tools in place prior to the use of URL shorteners are still relevant.
Hiding the real URL
The main argument against URL shortening services is that users don't know which domain they are being redirected to. In our previous example, users see the bit.ly host name in the link address, and do not know that they will be redirected to www.zscaler.com until after they click on the link. After the redirection, the ultimate destination URL can be seen in the web browser address bar.
How many people know the difference between a good URL and a bad URL? Even then, how can anyone be sure that a site won't serve malicious content. Many perfectly legitimate websites (Redcross, Indian Governmental websites, etc.) have been hacked and can contain an infamous hidden iframe to spread malware. Well-known websites are no longer necessarily safer than unknown or new sites. Simply using the reputation of the hostname for deciding whether a URL is safe or not is not a good idea.
In a post Michael wrote a year ago, he checked 100,000 TinyURL (URL shortener service) urls. He did not find any link to a malicious executable, no phishing sites, and really few redirections to malicious content.
I believe the danger of URL shorteners has been overblown, mainly based on the idea that individuals are in a position to determine if a website is dangerous or not simply by looking at the final URL. Users are far better off relying on antivirus, URL blacklists and regular browser updates for security. And these tools work just fine or shortened URLs as well.
There has been plenty of buzz about URL shorteners and security. URL shorteners have been described as a new attack vector since being popularized by social networks such as Twitter. I don't feel that URL shorteners are any more of a threat than their full length counterparts and here's why...
How URL shorteners work
The purpose of a URL shortener is to replace a log URL (e.g: http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html) with a shorter one (e.g: http://bit.ly/cikl0z). When a user clicks on http://bit.ly/cikl0z, he is redirected to http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html via an HTTP 301 redirection:
GET /cikl0z HTTP/1.1
Host: bit.ly
HTTP/1.1 301 Moved
Location: http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html
----------------------------------------------------------
GET /downloadwhitepaper_stateofweb-q4-2009.html HTTP/1.1
Host: www.zscaler.com
HTTP/1.1 200 OK
The browser made two requests: one to http://bit.ly/cikl0 and one to http://www.zscaler.com/downloadwhitepaper_stateofweb-q4-2009.html
Existing defense mechanisms
All the existing in-browser (Google Safe Browsing in Firefox, Opera's Fraud Protection, etc.) or external (IDS, proxy, etc.) URL scanners are applied on both the initial short and redirected long URL requests. If the long URL is a known malicious site, it will be stopped whether or not the the user clicks directly on the long URL, or on a shortened URL.
Also, content inspection (Antivirus, Deep Packet inspection, etc.) is applied on both requests.
The use of URL shorteners and redirections does not require any new security inspection. All of the web browser security tools in place prior to the use of URL shorteners are still relevant.
Hiding the real URL
The main argument against URL shortening services is that users don't know which domain they are being redirected to. In our previous example, users see the bit.ly host name in the link address, and do not know that they will be redirected to www.zscaler.com until after they click on the link. After the redirection, the ultimate destination URL can be seen in the web browser address bar.
How many people know the difference between a good URL and a bad URL? Even then, how can anyone be sure that a site won't serve malicious content. Many perfectly legitimate websites (Redcross, Indian Governmental websites, etc.) have been hacked and can contain an infamous hidden iframe to spread malware. Well-known websites are no longer necessarily safer than unknown or new sites. Simply using the reputation of the hostname for deciding whether a URL is safe or not is not a good idea.
In a post Michael wrote a year ago, he checked 100,000 TinyURL (URL shortener service) urls. He did not find any link to a malicious executable, no phishing sites, and really few redirections to malicious content.
I believe the danger of URL shorteners has been overblown, mainly based on the idea that individuals are in a position to determine if a website is dangerous or not simply by looking at the final URL. Users are far better off relying on antivirus, URL blacklists and regular browser updates for security. And these tools work just fine or shortened URLs as well.
Tuesday, March 9, 2010
Attackers going after end users rather than servers
From: http://www.networksasia.net/content/attackers-going-after-end-users-rather-servers
Rather than targeting Web and email servers, attackers these days are prone to going after enterprises from the inside out, compromising end user systems and then using them to access confidential data, according to a Web traffic analysis report by security-as-a-service provider Zscaler.
Based on a recent study of traffic passing through its global network, Zscaler's "State of the Web -- Q4 2009" report also notes trends including issues with botnets, corporate Internet access policies, and the use of the Internet Explorer 6 browser. Officially being released on Tuesday, the study analyzes Web traffic volumes covering several thousand Web transactions per second and hundreds of billions of Web transactions.
Zscaler found attackers were prone to embedding JavaScript or malicious iframes to pull content from an attacker's server, whereupon the content is rendered in a user's browser, said Mike Geide, senior security researcher at Zscaler, in an interview on Monday.
"The malicious content will then compromise the end user either through a vulnerable browser or through vulnerable client applications such as Adobe Acrobat Reader," Geide said. Malware then can steal victims' credentials.
"It's recommended that users take extra precaution when doing financial transactions online and if at all possible to utilize Web-based protection," Geide said. He acknowledged Zscaler offered services to remedy the issue but noted the company is not the only vendor to do so.
Zscaler also found significant use of the Internet Explorer 6 browser, even though it has been succeeded by two more secure generations of Microsoft's browser. Version 6, for instance, does not maintain malicious URL and phishing block lists, the report said.
Botnets present issues, according to Zscaler. "We're seeing a lot of botnets," Geide said. Zscaler blocks botnets, which can take over systems, said Geide. Zscaler also found some users attempting to deploy anonymizers, which hide a client IP address to enabie access to undesirable content such as gambling or pornography sites, he said.
Another issue, darknets, involves unallocated IP space and infected hosts on the network. This can lead to disclosures of internal information, said Geide. Also, attackers have launched phishing attacks from sites such as the recently removed fake social networking site, coolxd.com, according to Zscaler.
In other findings, Zscaler found that content such as JPEG and GIF was more prominent than JavaScript and HTML. "The Web is very media-rich at this point in time," Geide said.
Additionally, ZScaler found that the Firefox browser is slowly gaining wider adoption, although the company needs more time to determine precise browser usage trends. "Internet Explorer is still leaps and bounds ahead of Firefox as far as the enterprise user goes," said Geide. Firefox gained more than 6% in market share in December, Zscaler found. Still, Internet Explorer's share was at about 70% by the end of 2009.
Zscaler found Facebook predominant as a social networking site. Three-quarters of social networking traffic traversing the Zscaler network went to Facebook.
Rather than targeting Web and email servers, attackers these days are prone to going after enterprises from the inside out, compromising end user systems and then using them to access confidential data, according to a Web traffic analysis report by security-as-a-service provider Zscaler.
Based on a recent study of traffic passing through its global network, Zscaler's "State of the Web -- Q4 2009" report also notes trends including issues with botnets, corporate Internet access policies, and the use of the Internet Explorer 6 browser. Officially being released on Tuesday, the study analyzes Web traffic volumes covering several thousand Web transactions per second and hundreds of billions of Web transactions.
Zscaler found attackers were prone to embedding JavaScript or malicious iframes to pull content from an attacker's server, whereupon the content is rendered in a user's browser, said Mike Geide, senior security researcher at Zscaler, in an interview on Monday.
"The malicious content will then compromise the end user either through a vulnerable browser or through vulnerable client applications such as Adobe Acrobat Reader," Geide said. Malware then can steal victims' credentials.
"It's recommended that users take extra precaution when doing financial transactions online and if at all possible to utilize Web-based protection," Geide said. He acknowledged Zscaler offered services to remedy the issue but noted the company is not the only vendor to do so.
Zscaler also found significant use of the Internet Explorer 6 browser, even though it has been succeeded by two more secure generations of Microsoft's browser. Version 6, for instance, does not maintain malicious URL and phishing block lists, the report said.
Botnets present issues, according to Zscaler. "We're seeing a lot of botnets," Geide said. Zscaler blocks botnets, which can take over systems, said Geide. Zscaler also found some users attempting to deploy anonymizers, which hide a client IP address to enabie access to undesirable content such as gambling or pornography sites, he said.
Another issue, darknets, involves unallocated IP space and infected hosts on the network. This can lead to disclosures of internal information, said Geide. Also, attackers have launched phishing attacks from sites such as the recently removed fake social networking site, coolxd.com, according to Zscaler.
In other findings, Zscaler found that content such as JPEG and GIF was more prominent than JavaScript and HTML. "The Web is very media-rich at this point in time," Geide said.
Additionally, ZScaler found that the Firefox browser is slowly gaining wider adoption, although the company needs more time to determine precise browser usage trends. "Internet Explorer is still leaps and bounds ahead of Firefox as far as the enterprise user goes," said Geide. Firefox gained more than 6% in market share in December, Zscaler found. Still, Internet Explorer's share was at about 70% by the end of 2009.
Zscaler found Facebook predominant as a social networking site. Three-quarters of social networking traffic traversing the Zscaler network went to Facebook.
Friday, March 5, 2010
Hackers Sought Companies’ 'Crown Jewels'
From: http://www.businessweek.com/news/2010-03-03/mcafee-says-hackers-sought-crown-jewels-at-six-companies.html
March 3 (Bloomberg) -- McAfee Inc., exploring the cyber attacks originating from China, discovered at least six incidents in which hackers broke into the computer systems that companies use to house valuable intellectual property.
“We know that these systems were absolutely targeted for the crown jewels of each organization -- potentially representing billions of dollars,” George Kurtz, McAfee’s chief technology officer, said today in an interview from Santa Clara, California. “We want to shed light on a problem that many didn’t realize.”
Many companies hold source codes, product formulas and other kinds of intellectual property in “software configuration management systems,” said McAfee, the second-largest maker of security software. Companies typically set up these systems to support collaboration and version control, and they assume network security will keep their internal systems safe.
Google Inc., the world’s most-popular search engine, said in January that it found evidence of “sophisticated” cyber attacks originating from China. Hackers went after at least 20 companies, Google said at the time.
Those attacks are being investigated by U.S. government agencies, local law enforcement and security experts such as McAfee and larger rival Symantec Corp. McAfee Chief Executive Officer Dave DeWalt said this week that his company was the first to notice the hacks.
Non-Technology Companies
While Kurtz declined to say where the targeted companies are located, he did say they weren’t all technology businesses. Jill Hazelbaker, a spokeswoman for Mountain View, California- based Google, declined to comment.
McAfee fell 61 cents to $39.54 at 4 p.m. in New York Stock Exchange composite trading. The shares have slipped 2.5 percent this year.
The perpetrators of the attacks relied on an approach called spear phishing, targeting specific employees with high- level access privileges to the data they seek, Kurtz said. The hackers also learn the identities of people those employees trust and then send the employees e-mails, with infected attachments, pretending to be those people.
When the targeted employee clicks on an attachment, it triggers malware. That program opens a “back door” into the corporate network and steals passwords and other useful information, McAfee said.
“We saw that high-privileged users’ accounts were compromised, and that’s how the attackers got access,” Kurtz said. “If George has access to source code, I will figure out who’s friends with George and get him to click on something from that person.”
Most Valuable Information
Kurtz said few companies are adequately protecting their most valuable information.
“If companies had the same level of protections on their cash-management systems as they do on their intellectual- property repositories, they’d be broke,” he said. “We know of at least half a dozen companies that were targeted.”
Kurtz said he couldn’t confirm the source of the cyber attacks.
“It’s difficult to figure out,” he said.
--With assistance from Brian Womack in San Francisco. Editors: Stephen West, Nick Turner.
To contact the reporter on this story: Rochelle Garner in San Francisco at rgarner4@bloomberg.net
March 3 (Bloomberg) -- McAfee Inc., exploring the cyber attacks originating from China, discovered at least six incidents in which hackers broke into the computer systems that companies use to house valuable intellectual property.
“We know that these systems were absolutely targeted for the crown jewels of each organization -- potentially representing billions of dollars,” George Kurtz, McAfee’s chief technology officer, said today in an interview from Santa Clara, California. “We want to shed light on a problem that many didn’t realize.”
Many companies hold source codes, product formulas and other kinds of intellectual property in “software configuration management systems,” said McAfee, the second-largest maker of security software. Companies typically set up these systems to support collaboration and version control, and they assume network security will keep their internal systems safe.
Google Inc., the world’s most-popular search engine, said in January that it found evidence of “sophisticated” cyber attacks originating from China. Hackers went after at least 20 companies, Google said at the time.
Those attacks are being investigated by U.S. government agencies, local law enforcement and security experts such as McAfee and larger rival Symantec Corp. McAfee Chief Executive Officer Dave DeWalt said this week that his company was the first to notice the hacks.
Non-Technology Companies
While Kurtz declined to say where the targeted companies are located, he did say they weren’t all technology businesses. Jill Hazelbaker, a spokeswoman for Mountain View, California- based Google, declined to comment.
McAfee fell 61 cents to $39.54 at 4 p.m. in New York Stock Exchange composite trading. The shares have slipped 2.5 percent this year.
The perpetrators of the attacks relied on an approach called spear phishing, targeting specific employees with high- level access privileges to the data they seek, Kurtz said. The hackers also learn the identities of people those employees trust and then send the employees e-mails, with infected attachments, pretending to be those people.
When the targeted employee clicks on an attachment, it triggers malware. That program opens a “back door” into the corporate network and steals passwords and other useful information, McAfee said.
“We saw that high-privileged users’ accounts were compromised, and that’s how the attackers got access,” Kurtz said. “If George has access to source code, I will figure out who’s friends with George and get him to click on something from that person.”
Most Valuable Information
Kurtz said few companies are adequately protecting their most valuable information.
“If companies had the same level of protections on their cash-management systems as they do on their intellectual- property repositories, they’d be broke,” he said. “We know of at least half a dozen companies that were targeted.”
Kurtz said he couldn’t confirm the source of the cyber attacks.
“It’s difficult to figure out,” he said.
--With assistance from Brian Womack in San Francisco. Editors: Stephen West, Nick Turner.
To contact the reporter on this story: Rochelle Garner in San Francisco at rgarner4@bloomberg.net
Subscribe to:
Posts (Atom)


