People surf to a number of web pages throughout the day - online shopping, banking, social networking, search engines, etc. But do they know when something bad is happening behind the web page visible in their browser? A large number of legitimate web sites have been victim of attacks, where the payload modifies the pages on the website to include hidden Iframes to malicious content. This content is processed by the browser, transparent to the user, and can compromise the user’s system if they are running vulnerable client applications (for example, the browser itself, browser plug-ins, Adobe Acrobat reader, and Flash player).
Malicious Iframe attacks are not new but remain heavily used to carry out different attacks. HTML Iframe tags are used to embed content into the web page from a particular source, including sources external from the actual web site. Attackers are using zero pixel Iframes embed malicious content while to keeping content hidden from the user. People are often become victims from such attacks as it is easy to inject such malicious Iframes into a legitimate webpage by taking advantage of web application vulnerabilities like SQL injection.
Let’s walk through live example where a malicious Iframe has been injected in the webpage. Here is the screenshot of one of the website injected by Iframe,

The above screenshot shows obfuscated JavaScript is present in the webpage after the closing html “” tag (prior to the actual page body). Malzilla a user friendly GUI tool was used to decode the obfuscated JavaScript. You can find good documentation on their website.

Interestingly, the JavaScript decodes into another obfuscated JavaScript. There is small function called dF() and a call to the “document.write()” function. Below is a screenshot of decoding this further:
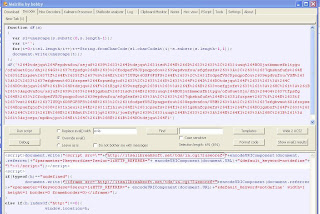
After decoding a second time, the JavaScript is clear and readable. This hidden injected Iframe embeds this JavaScript within the page, and when someone visits the page the JavaScript is processed by the browser, transparent to the user. If you look at the height and width of the Iframe, it is set to 1 pixel, which will not be seen by the user.
The above live example used multiple obfuscation techniques to hide the functionality of the malicious JavaScript. We have seen a number of websites infected with the same JavaScript code. The above example used “document.write()” function to write the malicious script into the page. Below is a decoded single obfuscated JavaScript example, which is still present on many websites:

Attackers are using simple to complex obfuscation techniques to encode their malicious script. Due to this, many Antivirus engines are unable to detect new injected Iframes. Here are the Virustotal results for the first example showing very low detection. Here is the third example of injected obfuscated script:

There are some important points to be considered here.
* In the past, it was common for attackers to inject their malicious Iframes at the bottom / end of the webpage. Attackers are now injecting malicious Iframes anywhere in the webpage.
* Many websites which were found to be infected in past months by malicious hidden Iframes appear to still be infected with them. Meaning most web site owners or hosting providers are not policing the content that they are serving on the web.
Our data shows many previously infected websites are still infected with hidden malicious Iframes today. Due to different obfuscation techniques detection by Antivirus vendors remains poor. This shows that even if it is a well-known attack, people are still at risk of being compromised. Web site owners and hosting providers should regularly patch any 3rd party web applications used to avoid known vulnerabilities (such as SQL injection), and regularly inspect their web pages for unauthorized modification (to include these malicious Iframes). Look out for obfuscated JavaScript within webpage’s, and for additions made prior to or following the HTML body tags. Users should patch all client applications (browsers, browser plug-ins, Adobe Acrobat, Flash, Java, Microsoft Office, etc.) used to view content pulled from the web. Additionally users can inspect the source of webpage and report compromised sites to the web site owner or hosting provider.
Start acting now. Be Safe while surfing!



No comments:
Post a Comment